Emerging Ransomware Trends in 2022
The new year brings new operating models, highly targeted attacks, and additional battlegrounds into the ransomware business.

Ransomware is a global cyber threat affecting individuals, businesses, and government entities. Most experts agree that the ransomware industry is still growing in 2022, and consequently, organisations will continue paying a high price in damages and lost revenue. Furthermore, the new year brings new operating models, highly targeted attacks, and additional battlegrounds into the ransomware industry. Therefore, decision-makers need to seek innovative technologies to protect their organisations from evolving threats in 2022.
The Ransomware Status Quo
According to a recent Sophos survey, one in every three organisations was impacted by a ransomware attack in 2020. In addition, Sophos reports that organisations paid a U$170,404 ransom on overage to get the encrypted files back and a whopping U$1.85 million to remedy the outcome of the cyber-attack.
Apart from the financial losses, organisations reported other damages, including lost data, lost productivity, lost revenue, and disrupted business operations. Sophos, to illustrate how widespread the ransomware problem is, the cybersecurity firm reports that 79% of their incident response engagements are related to ransomware attacks. In summary, organisations are already paying a hefty price to fight ransomware.
Ransomware Down Under
In Australia, the ransomware situation is similar to the global experience. According to the Australian Cyber Security Centre (ACSC), ransomware-related incidents grown steadily since the 2017 WannaCry campaign.
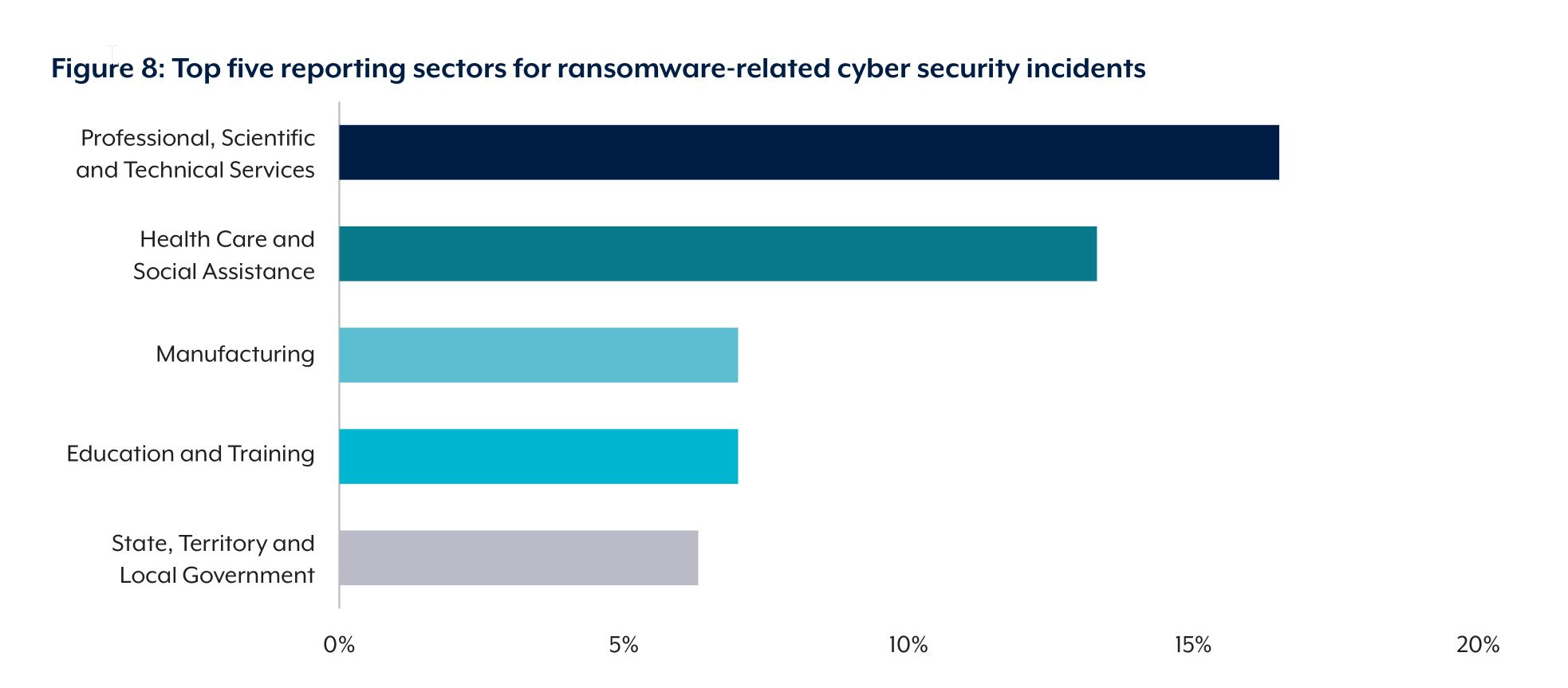
According to the ACSC Annual Cyber Threat Report 2020-21, Australian organisations reported about 500 ransomware incidents to the ACSC, which is a 19% increase compared to the previous period. The ACSC suggests that healthcare, government, education, and transport are the most affected sectors.
In conclusion, the current trends of the ransomware business in Australia fit into the international trends.
Ransomware Trends in 2022
Numerous reports of top cybersecurity firms unanimously predict an increase in ransomware incidents for 2022. Sadly, these reports all anticipate further sophistication of the ransomware campaigns and more damage.
Bespoke Ransomware Campaigns
According to Trend Micro, ransomware attacks are becoming increasingly targeted ever than before. In other words, ransomware operators are tailoring their code to the victim’s security posture, as the Sophos Rapid Response Team confirms.

In this new operating model, highly skilled ransomware developers work day and night to craft the perfect ransomware code for each victim. Instead of being a 'jack of all trades and a master of none', ransomware developers lease their heavily-customised ransomware code to other criminals with expertise in ransomware distribution.
The new two-layer ransomware model is known as Ransomware-as-a-Service, or simply RaaS.
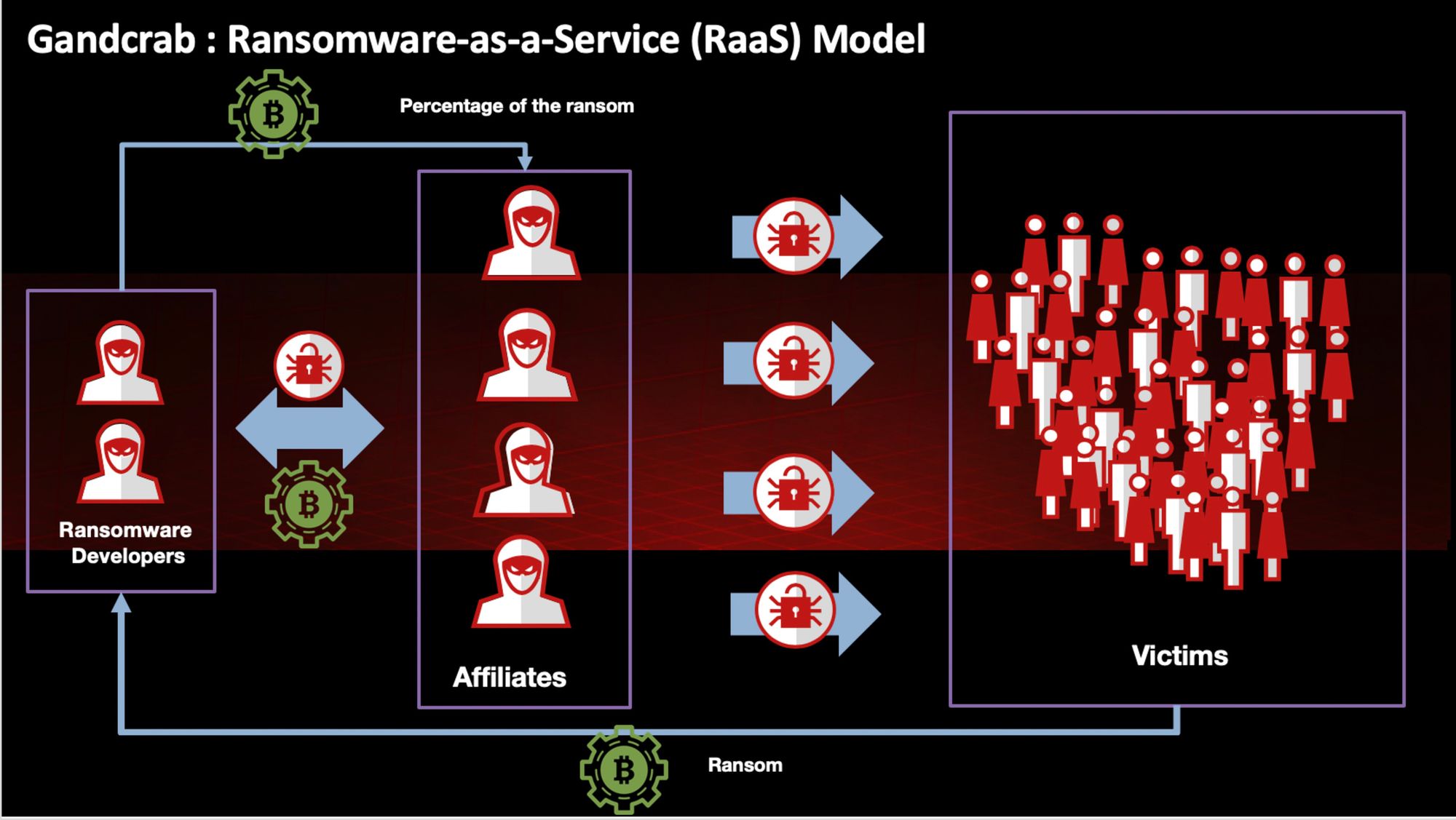
The bad news is that this business model drives criminal groups into a high level of specialisation in the ransomware business. What makes the RaaS approach particularly evil is the new heights in sophistication that goes into every phase of the ransomware business.
In a nutshell, ransomware operators are shifting from the less sophisticated, opportunistic attacks towards highly customised ransomware campaigns.
Small Businesses are in the Crosshairs
Because of the new RaaS operating model, small and medium-sized businesses need to up their guards in the new year to avoid a ransomware attack.
One expert at the cybersecurity firm, Arctic Wolf, predicts that ransomware operators will aim for smaller targets than large enterprises. It is probably known that a technology gap exists between well-funded enterprises and smaller businesses in the SMB sector. As a consequence of this imbalance, smaller companies have fewer security resources and ultimately defend their organisation from the ransomware threat.

In conclusion, ransomware operators will see smaller businesses as easy targets compared to better-funded corporations. Therefore, the SMB sector needs to increase their cyber spending to combat the growing threat.
Superintelligence in the Ranks of Ransomware
Lastly, the cybersecurity firm, Sophos, warns of the latest Artificial Intelligence (AI) and Machine Learning (ML) trends in the context of ransomware. According to the firm, more AI and ML-powered technologies have recently become more accessible to the adversaries. The new AI/ML tools allow criminals to generate an untold number of ransomware variants at a much lower cost than before.
In addition to lower costs, the Sophos Threat Report speculates that further AI/ML technologies such as voice synthesis, image generation and deepfake algorithms will boost watering-hole-type phishing attacks in the future.
Ransomware Moves to Cloud 9
Cyber reports also expect ransomware campaigns to focus on other building blocks of the enterprise ICT architecture. For instance, Trend Micro predicts that ransomware campaigns will target cloud-based environments more since organisations rely on the cloud more than ever.

Ransomware versus cloud-based platforms are nothing new. For example, Jigsaw was encrypting files on OneDrive, or a hacker named ‘Harak1r1’ was holding public unsecured MongoDB databases to a ransom. Criminals already found that cloud-based platforms can open new revenue streams to their ransomware business.
Despite the forecast of cloudy skies, Trend Micro warns that organisations should keep protecting their on-premises environments as the classic ransomware attack vectors – such as spear-phishing emails, VPNs, and remote desktop (RDP) – will persist in the future.
Data Leaks are the New Currency
Last but not least, the next big thing that makes ransomware campaigns more devious is the new extortion vectors. Criminals found that the threat of a data breach makes the victims more likely to pay up the ransom in the classic model.
When a classic old-fashioned ransomware variant swung into action, all files on the disk were made unavailable with encryption. The ransomware operators were essentially selling the decryption keys in exchange for a sum of cryptocurrencies.
Organisations learned the hard way that data backup is an effective measure against ransomware attacks because this is the only way to get the files back with a high chance of success. The ACSC do not recommend organisations paying the ransom as there is no guarantee that the files can be recovered, and payments tend to encourage further attacks.
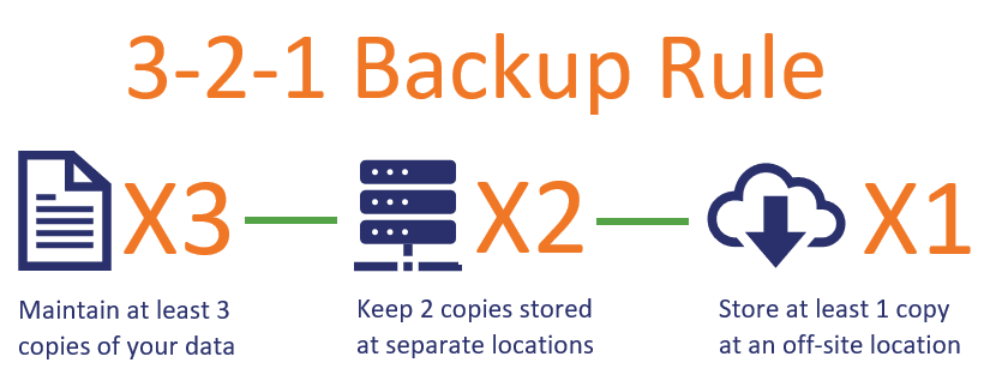
Therefore, organisations with a successful anti-ransomware strategy used to rely on backups rather than ransom payments. As a result, it became less likely for the criminals to achieve their financial goals, which made them innovate how money is made. To make ends meet, ransomware operators have found a new way to motivate payments.
The late trend in the ransomware world is that new variants are waiting days or weeks before the file encryption process begins. In the meantime, ransomware operators with a foothold on the victim’s ICT infrastructure start looking for sensitive files, documents, emails, and anything of value. Once the operators finish exfiltrating the digital assets to the cloud under the criminal’s control, they trigger the classic file encryption process.
As a result, criminals have two leverages against the victim:
- The decryption keys for the recovery of the encrypted files; and
- The confidential data stolen from the organisation.
The ransomware operator would then threaten the victim with releasing sensitive files, documents, and emails on the dark web for everyone to see unless the ransom is paid. Even when an organisation has good backups and the encrypted files could be restored with no effort, the victim still faces a dilemma as the public release of sensitive data can be devastating.
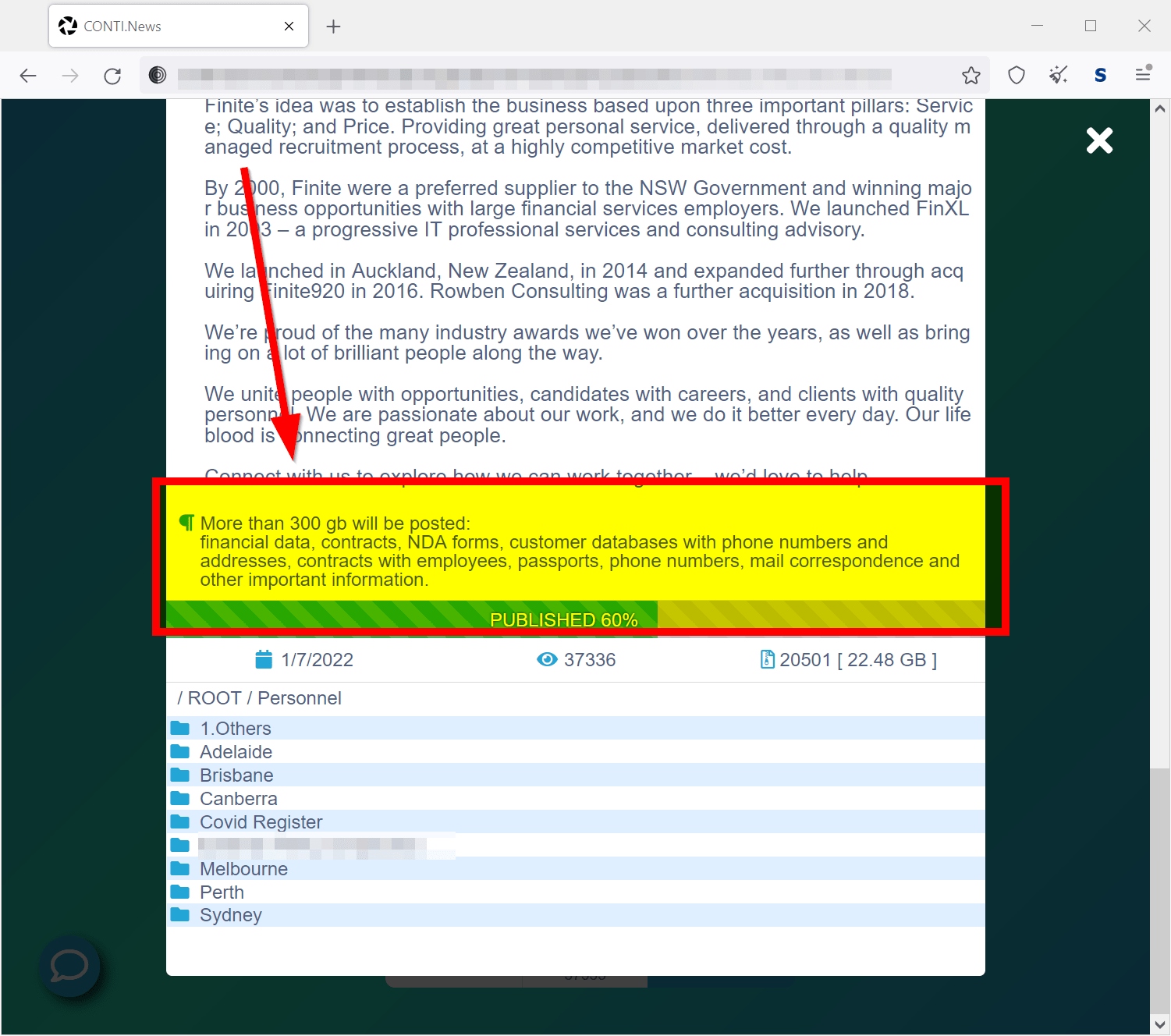
A recent example of this scheme is the recent case of the Australian recruitment company named Finite, where the ransomware operators have managed to steal a large amount of data. After the data theft, the criminals were threatening to release the resumes, contracts, personal documents, and other sensitive details of the candidates and the hiring organisations unless Finite paid the ransom.
In the annual data breach of Verizon, the firm confirms that 10% of the reported data breaches can be attributed to this ransomware money-making scheme. The new steal-and-extort ransomware approach spiralled ransomware attacks to the top reasons behind data breaches.
To sum up, organisations should prepare for the consequences of a potential data breach more than ever.
Conclusion
In summary, organisations of every size should prepare an upwards trend in ransomware operations. Emerging trends, such as the Ransomware-as-a-Service operating model, bespoke ransomware attacks, Artificial Intelligence and Machine Learning, all bring in a new level of sophistication to the ransomware business. Therefore, apart from the standard security advice against ransomware attacks, organisations should look for innovative techniques to protect themselves from the latest ransomware trends in 2022.
This post is based on my essay written for the Charles Sturt University.

