Two Innovative Ways to Combat Ransomware
We all know the seven traditional steps to fight ransomware, but are they still holding up?

We all know the seven traditional steps to fight ransomware, but are they still holding up? Also, how do they scale in the cloud? In the following article, we briefly look at the infrastructure as code and the zero-trust models and how your ransomware strategy can benefit from them.
Infrastructure as Code
The Infrastructure as Code (IaC) approach can enable organisations to fight ransomware on their cloud platforms. IaC has been around for about a decade allowing IT professionals to deploy and operate complex cloud environments with no effort.
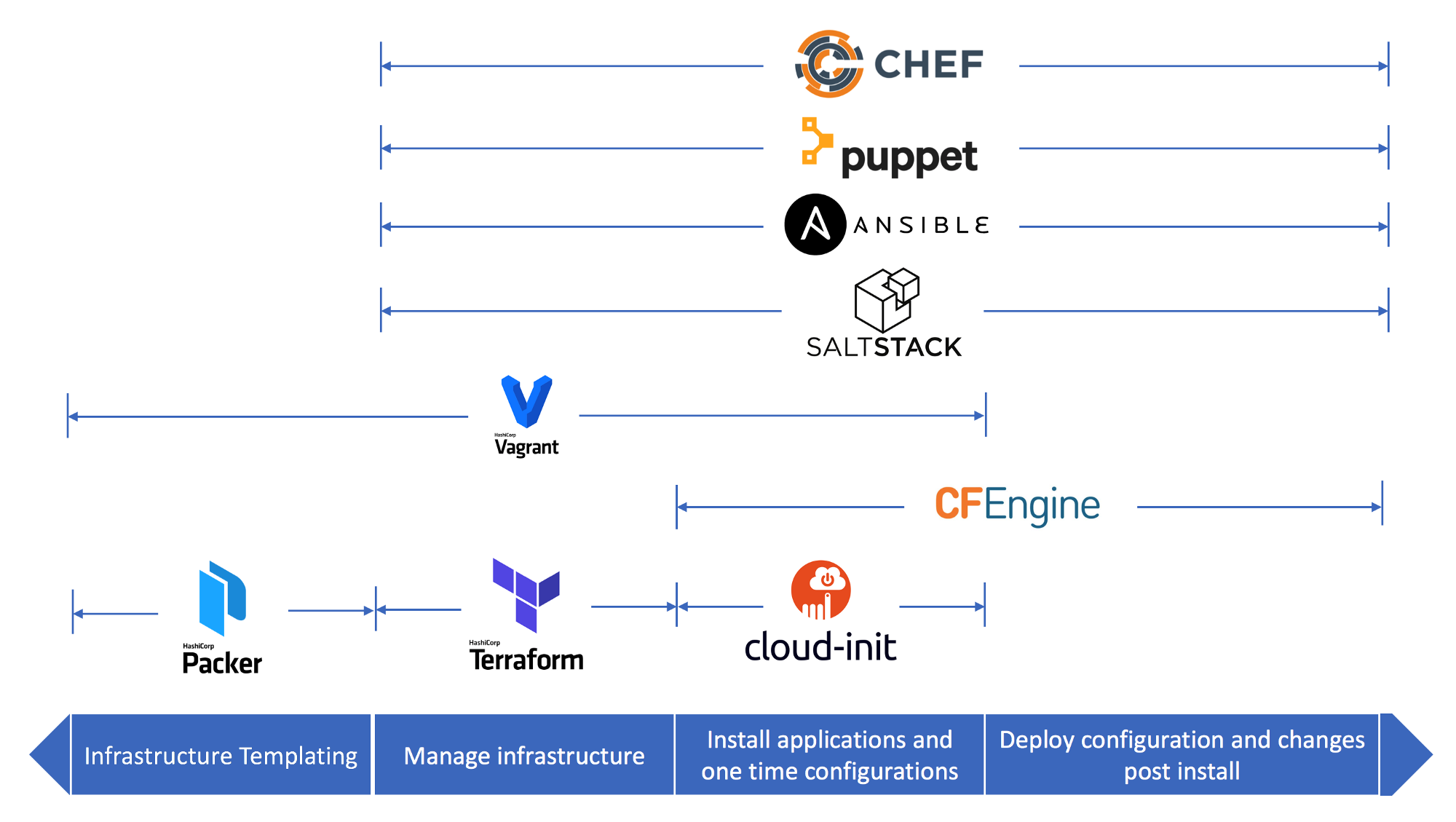
IaC Security Benefits
What IaC also allows is the implementation of a robust cloud-security baseline in an automated, repeatable, and verifiable manner. With everything is written in code, organisations can deploy their cloud infrastructures with good security and anti-ransomware practices by default.
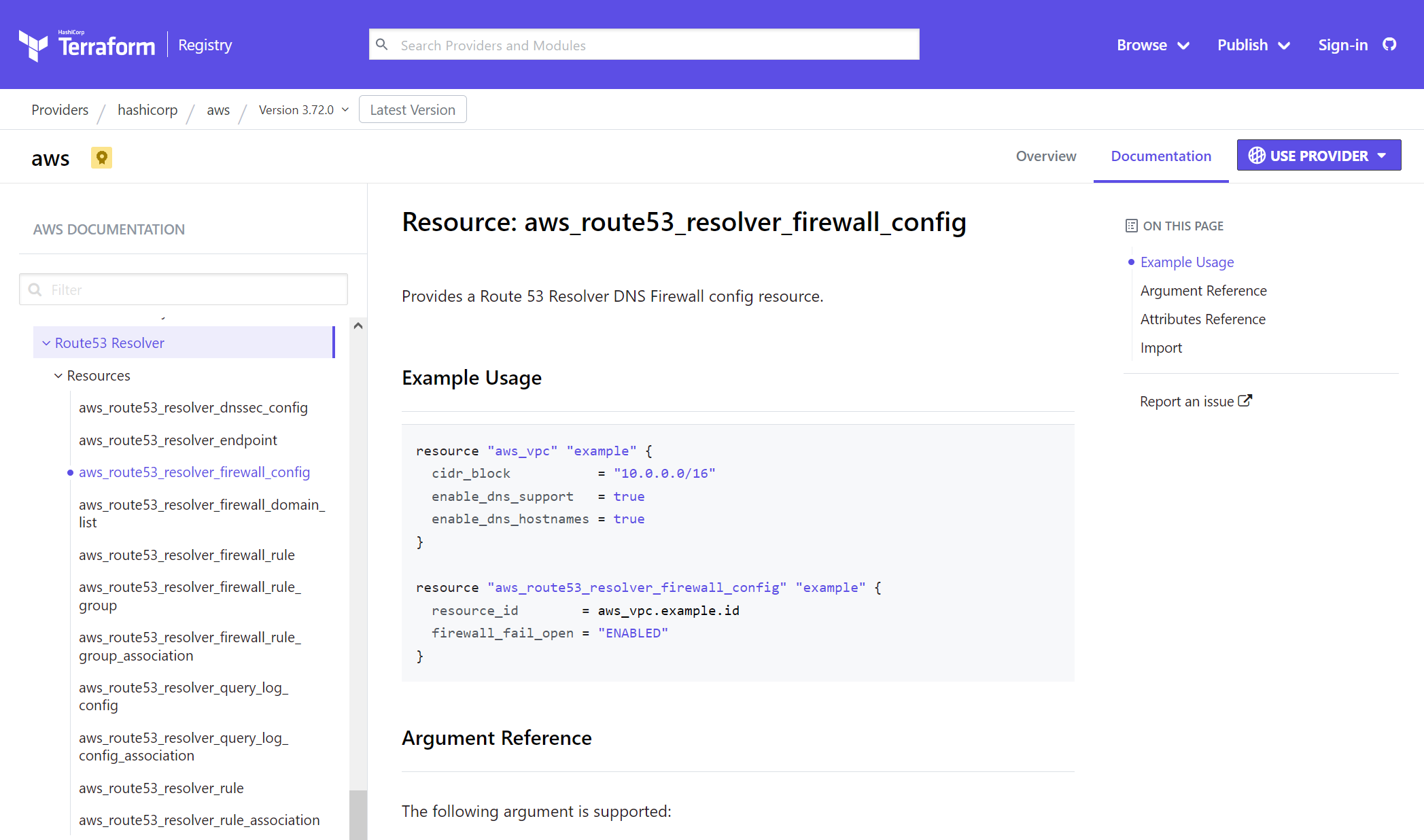
Unfortunately, public cloud environments like AWS and Azure usually have a plethora of cloud-native security features, but they are disabled out-of-the-box protecting nothing. With the IaC approach, cloud engineers can cut through the complexity of the AWS/Azure dashboards and link these add-on services to any cloud resources with a few keystrokes. For example, it takes a few lines of code to enable the Route 53 Firewall service with Terraform.
Furthermore, the IaC approach can guarantee that cloud environments are future-proof in terms of security as the threat landscape evolves. For example, developers can easily fine-tune their IaC codebase if a new ransomware threat emerges.
Managing Security with IaC
With the standard DevOps toolchain, IaC products such as AWS CloudFormation, Ansible and Terraform, IT professionals can:
- Enable public and private cloud platform security and backup features;
- Manage convoluted network architecture designs; and
- Apply secure configuration settings to operating systems and applications.
As it is known, a good backup strategy is a must to recover the encrypted files after a ransomware attack. With the appropriate IaC tooling, cloud-native backup services like Amazon Data Lifecycle Manager, AWS Backup or Azure Backup are easy to enable on all critical resources.
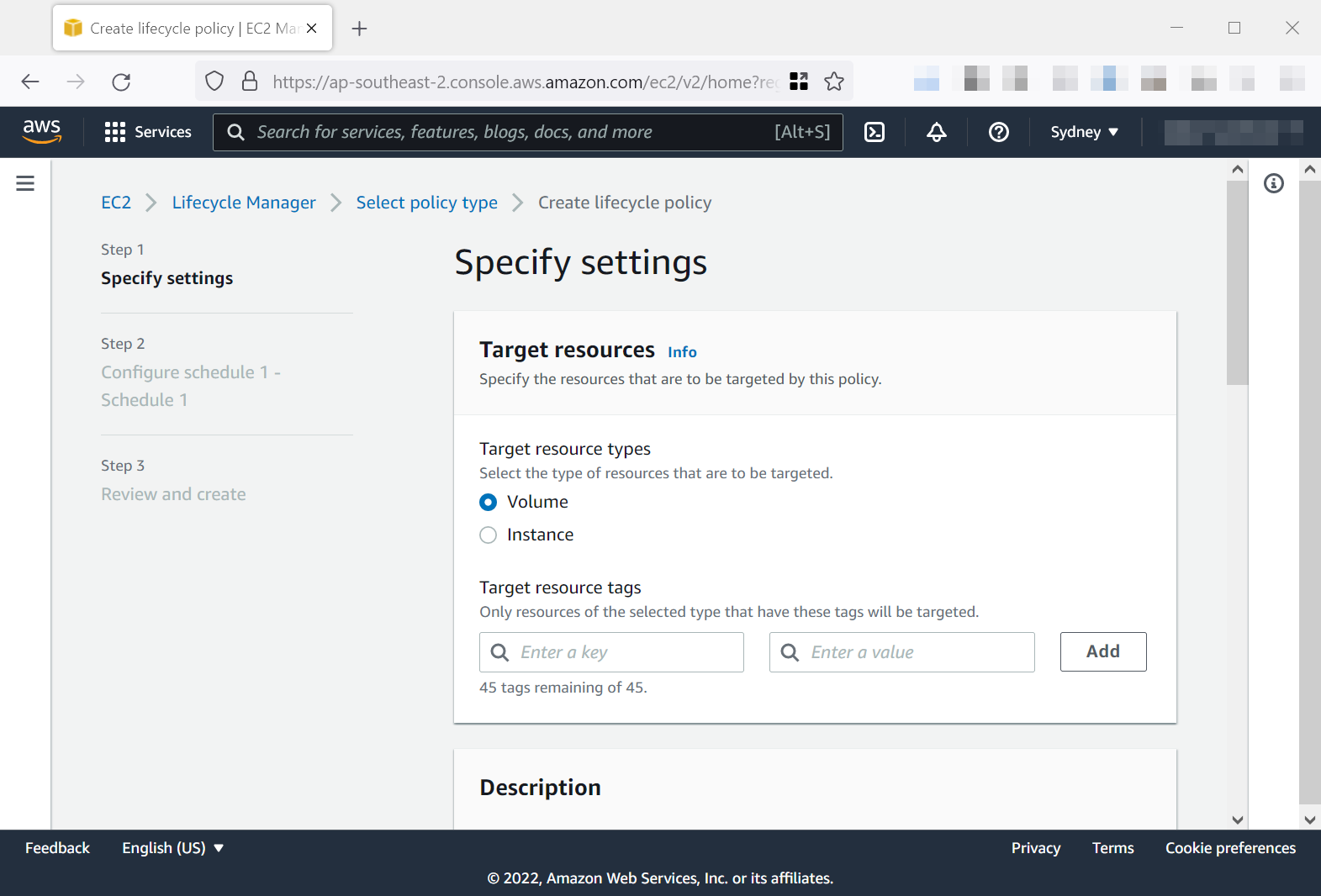
As for patching, tools like Terraform makes it easy to create new VMs on the Microsoft Azure platform with the 'automatic updates' feature enabled. In addition, Terraform can manage patch baselines and patch groups of the Systems Manager Patch Manager service on Amazon Web Services.
Modern IaC tools can deploy and configure other cloud-native security services fighting ransomware. For instance, Azure Defender and the previously mentioned Route 53 malware-blocking DNS firewall are both desirable security measures against ransomware activity, according to Microsoft and Amazon. Moreover, DevOps engineers can enable both services easily with just a few lines of code.
The Zero Trust Model
Various ransomware mitigation strategies suggest implementing the zero trust model as an effective measure in both on-premise and cloud environments.
The traditional network architecture design pattern assumes that the internal network is safe, and the bad actors on the internet are kept outside the network perimeter. Nonetheless, ransomware campaigns like WannaCry and NotPetya have demonstrated the flaws of this conventional approach to network design.
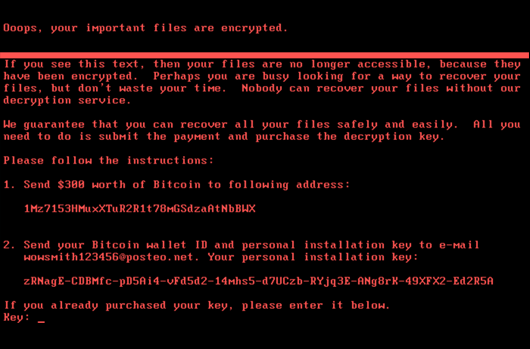
Today, we know that both ransomware variants relied on a vulnerability in the Server Message Block (SMB) protocol of the Windows operating system. The 'EternalBlue' vulnerability enabled WannaCry and NotPetya to spread across poorly segmented computer networks quickly. Additionally, internal networks with a low level of network segmentation were particularly vulnerable to these ransomware variants as a single compromised Windows machine could infect computers en masse with no control.
One answer to the poor network segmentation is the zero-trust network model. The traditional network design paradigm assumes that the network perimeter isolates 'safe' and the 'unsafe' network segments. On the other hand, zero-trust assumes that an adversary always persists within the internal network, and IT practitioners should design the various security controls accordingly.
In summary, the zero trust model aims for an extreme level of segmentation (i.e. trusting nobody) to reduce the "blast radius" if a security incident happens. For instance, organisations embracing the zero-trust security strategy could contain the WannaCry and NotPetya spread to a tiny network segment only.
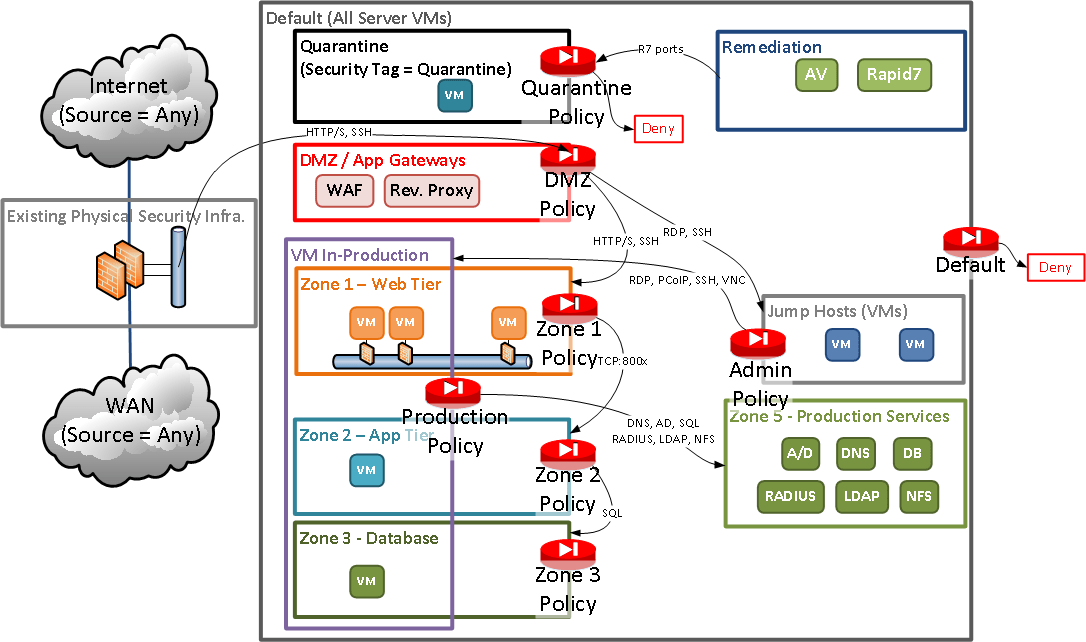
Although implementing network boundaries (firewall rules, routes, subnets, etc.) is probably a daunting exercise, IaC can streamline the process. Firstly, IaC tools can deploy premium firewalls such as Azure Firewall or AWS Network Firewall and its associated access control lists. Secondly, the implementation of VPCs, network routes and subnets, gateways, security groups and ACLs is a child's play regardless of their size or complexity. In conclusion, he IaC approach can take zero-trust to the extreme with relative ease.

