Don't Be the Next Business to Fall Victim to a Data Breach
Ninety per cent of data breaches begins with a phishing attack and email scams cost Australian businesses $22 million a year. But what is phishing and how does it differ from spam?

Ninety per cent of data breaches begins with a phishing attack and email scams cost Australian businesses $22 million a year. But what is phishing and how does it differ from spam?
The terms spam and phishing both describe different types of unwanted email businesses may receive, but there are key differences that businesses need to be aware of to avoid becoming the next data breach scandal. While spam is merely a general nuisance, phishing can cost your company $100,000 per incident.
Spam is generally easy to identify as unwanted email and does not contain any malicious intent in general. We are probably all familiar with emails trying to sell counterfeit pills and shifty SEO services.
Phishing, on the other hand, gives the appearance of coming from a trusted source, but contains malicious content, such as:
- Viruses or ransomware; or
- Malicious links which trick the recipient into handing over their passwords in order to gain unauthorised access to a system.
To quote one of our cybersecurity experts at Iron Bastion:
Phishing is a social engineering technique used to get a foothold within a company. Criminals use that foothold to hack the company from the inside to steal money or customer data, to defraud clients, and to commit payment redirection fraud or Business Email Compromise Fraud.
For businesses, phishing attacks constitute a serious threat. According to research, phishing attacks are the number one precursor to data breaches.
If your business has an annual turnover of over $3 million, it is subject to the Privacy Act 1988 (Cth) and the recently introduced Notifiable Data Breach Scheme. In circumstances of sensitive personal information being stolen, your organisation may be required to notify of the breach regardless of annual turnover.
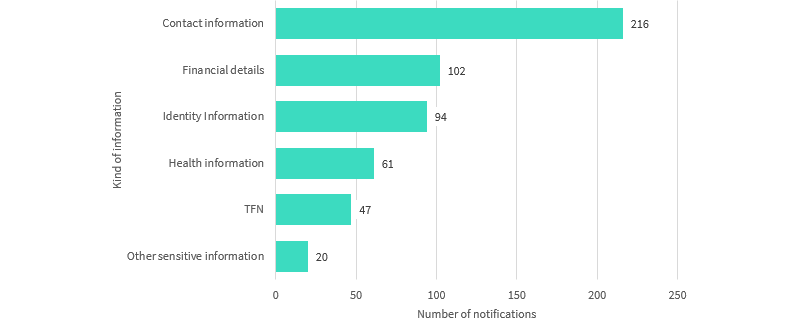
For instance, if your staff receive personal documents over emails for 100 point checks on a regular basis, a single compromised mailbox would trigger the mandatory reporting obligation. See the Office of the Australian Information Commissioner advice to clarify your reporting obligations further.
Why Outdated Advice Will Not Protect You
According to Iron Bastion, the spam problem has mostly been solved with mathematics and technology with the use of Bayesian spam filtering. All modern email hosting providers use these spam filters and are tightly integrated into their service offering.
Phishing, on the other hand requires a multifaceted approach and cannot be eliminated with Bayesian filtering. Because phishing emails are designed to look like other legitimate emails it requires a combination of human and technological solutions. Cybersecurity awareness training courses, phishing simulation exercises and anti-phishing technologies are examples some of these solutions.
Sadly, "common sense" tips are ineffective (read more) to combat phishing as organised cybercriminals possess multiple technical and soft skills these days. If these top tips were effective, phishing sites would be on the increase year after year in the past decade according to Google Safe Browsing.
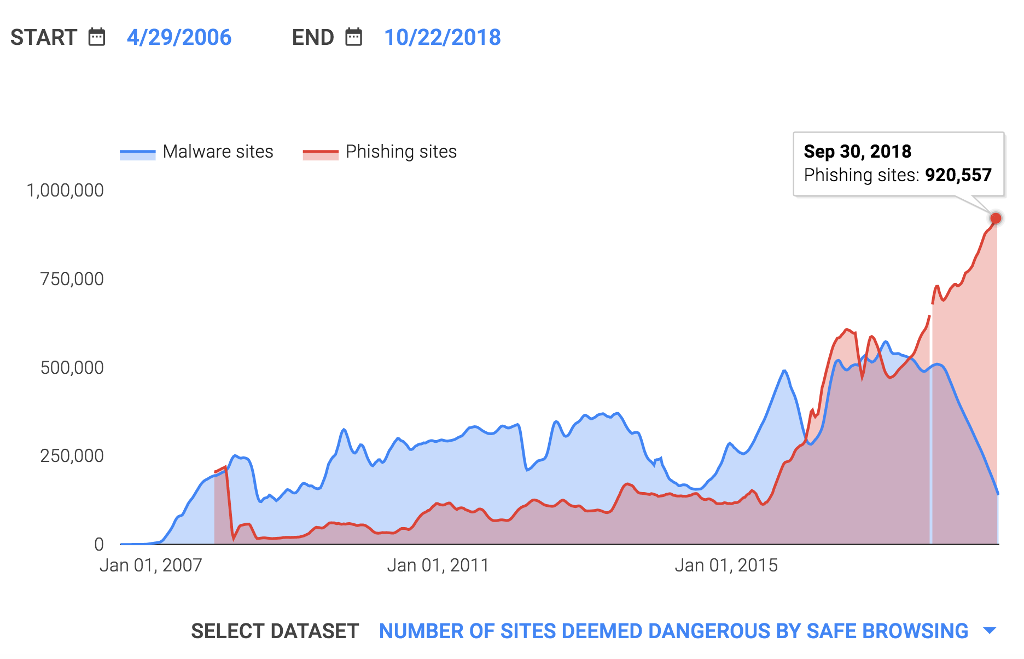
Cybercriminals can speak perfect English, are familiar with the industries they target, and use terminology informed by insider knowledge. Such sophistication is motivated by the profitability of cybercrime which exceeds that of the drug trade. This is why phishing awareness training for employees is so important. Your staff should be trained to recognise the most common scams, as employees are the last line of defence when your business is in the cross hairs of organised criminals.
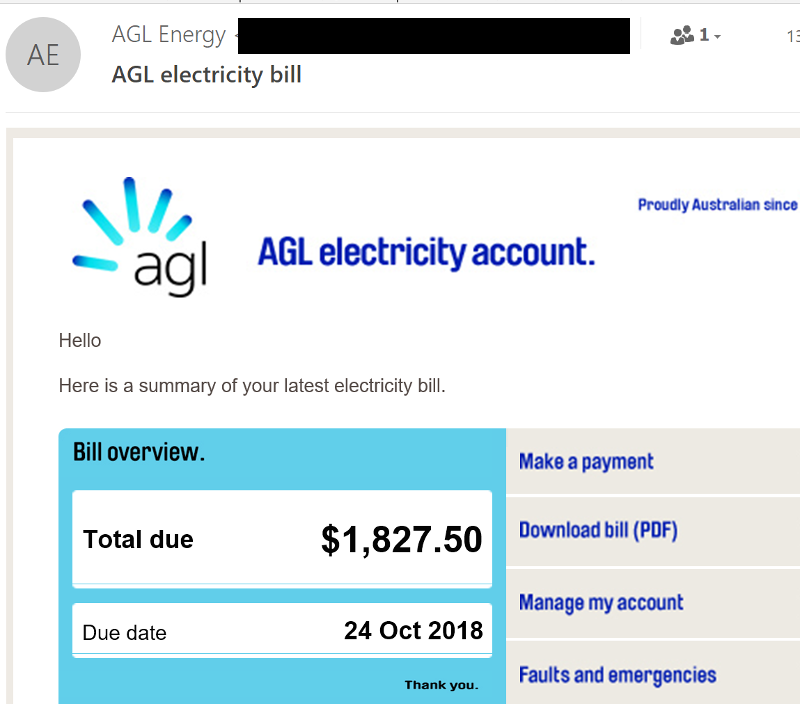
How Awareness Training Can Protect Your Business
Organisations are not powerless to deal with phishing, there are steps that any business can take. Firstly, organisations need to understand the risks they are most likely to face. For example, healthcare firms might be targeted for health information or with ransomware, whereas conveyancing firms are targeted with payment redirection scams.
This is where cyber security awareness training for your staff plays an essential role. Training can be tailored to your organisation’s particular risk profile. You can use the training to identify and understand segments of your staff vulnerable to social engineering with phishing simulation and then educate at-risk staff with appropriate content. Cybersecurity awareness training can be classroom based, or delivered via e-learning platforms.
We have previously published some tips to help you identify phishing attempts: https://blog.ironbastion.com.au/five-ways-to-detect-phishing-emails/
Once initial phishing awareness training has taken place, Iron Bastion recommends running a follow-up phishing simulation (with the consent of management) to test the vulnerability of email-based social engineering attacks, and to measure the effectiveness of training. Phishing simulation and cyber security awareness training should be run at regular intervals along with other regulatory and compliance training in your organisation.
About Iron Bastion
Iron Bastion are Australia’s cybersecurity experts. We provide cybersecurity solutions and data breach investigation services. Our team are qualified cybersecurity professionals, and all our staff and operations are based in Australia.
Contact us in confidence for a free cyber security consultation.

