A Scam Which Preys on Vulnerable People (and Works!)
This phishing campaign is a prime example of how heartless cybercriminals prey on vulnerable people

This phishing campaign is a prime example of how heartless cybercriminals prey on vulnerable people.
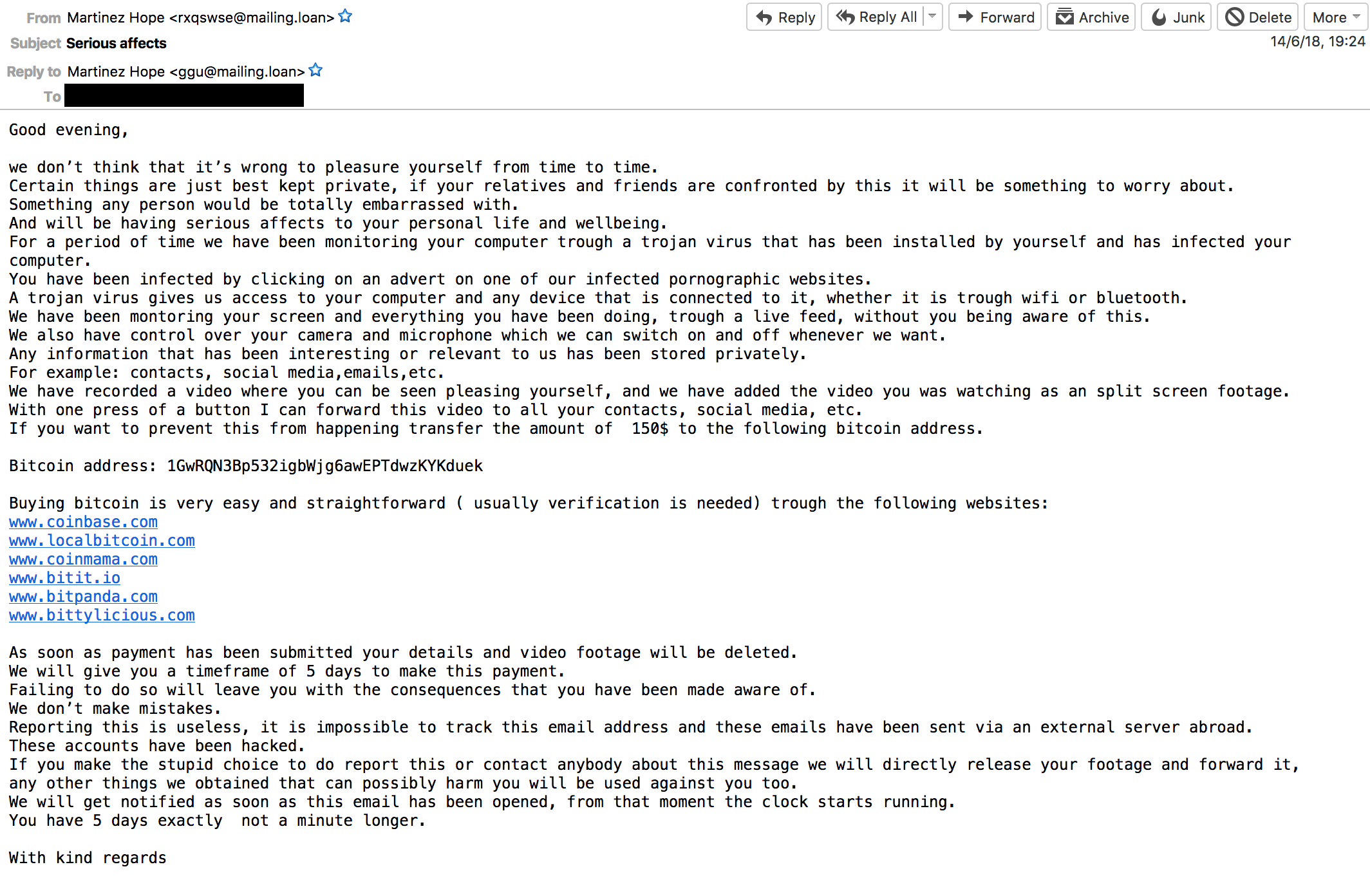
Our experts have been made aware of a new email extortion scheme targeting Australians. The email suggests that a backdoor has been installed on the victim's computer and the user was caught red-handed while pleasuring him or herself. The scammers then threaten to send the video evidence to everyone on the victim's contact list destroying his or her reputation unless a ransom of $150 (0.02 BTC) is paid to a specific Bitcoin wallet.
First of all, there is nothing to worry about.
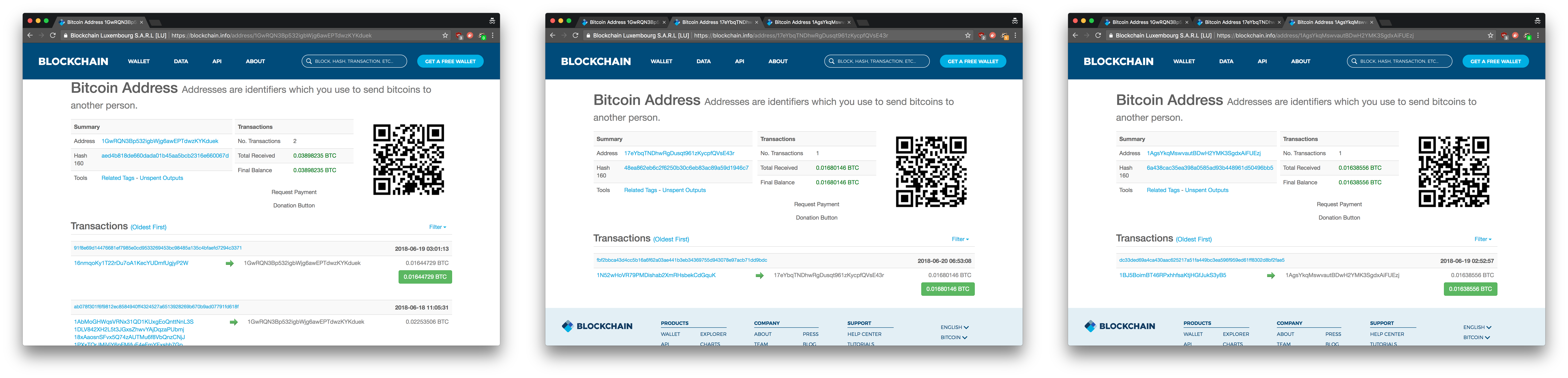
Sadly, the victims are paying up.
By inspecting the Bitcoin wallets associated with this campaign, it seems that some of the victims have chosen to pay the ransom. The pretext[1] of this extortion scheme is built on the malware-scare, which makes the whole scenario authentic – and it works. Probably the most impressive thing is that the campaign does not rely on any malware-infected file attachments or dodgy web links to trick victims.
Please pass the word on to raise awareness of this vicious phishing campaign and let everyone know it is merely a scam and there is nothing to worry about.
Phishing campaigns like these are harmless and the emails are safe to be ignored.
About Iron Bastion
Iron Bastion are Australia’s anti-phishing experts. We offer all businesses the same anti-phishing technology used by big businesses, without the big-business pricing.
We offer a range of anti-phishing services which are cloud-based, fully managed and easily integrate with your existing infrastructure. Our team are qualified cybersecurity professionals, and all our staff and operations are based in Australia.
Contact us for a free consultation, or sign up for a 14-day free trial of our services today.
A social engineering technique where cybercriminals fabricate a believable scenario ↩︎