Professional Help Needed for Law Firms Still Vulnerable to Phishing Attacks
Many of the leading law firms are failing set-up the anti-phishing solution correctly at their end, leaving them open to cyberattacks including phishing, payment redirection fraud and Business Email Compromise (BEC) fraud – our latest report can reveal.

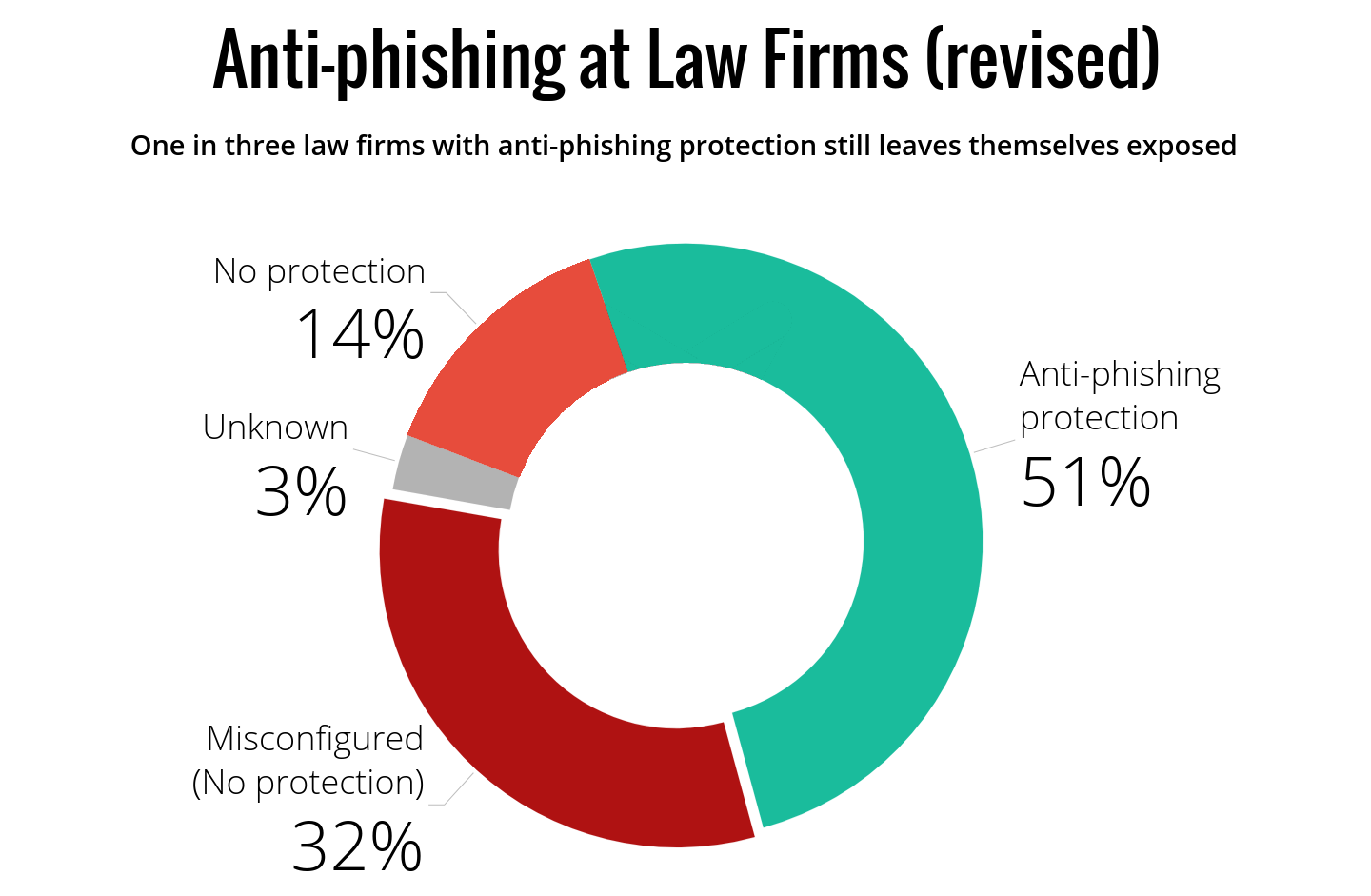
Despite the widespread uptake of advanced anti-phishing solutions by 83% of Australia’s law firms (Szathmari and Kavadias 2018), the experts behind Iron Bastion have revealed in their latest report that many of these leading organisations are failing set-up the anti-phishing solution correctly at their end, leaving them open to cyberattacks including phishing, payment redirection fraud and Business Email Compromise (BEC) fraud.
Anti-phishing solutions work (ideally) by running the incoming email flow to the firm through the anti-phishing service, so that only emails that have been cleared of malicious content are received by employees of the organisation using the anti-phishing service.
In the report released today, Iron Bastion share their finding that even where anti-phishing services are purchased and in use, there are a significant number of law firms that fail to properly implement that service.
Organisations in the legal industry spend thousands of dollars a month on advanced anti-phishing solutions yet without the correct set up at their own end, the impact is twofold. The organisation remains open to threat with employees unaware that their emails may be from a malicious source, and tens of thousands of dollars are wasted on creating a false sense of security.
Iron Bastion have labelled this exploit ‘Direct Email Spool Attack’ and while it sounds complex, it works simply by exploiting a failure to restrict the IP addresses on the recipient servers to those operating the upstream anti-phishing service.
Iron Bastion were able to model a type of attack which relies on incorrect settings on the internal email gateways accepting emails from the anti-phishing service. In parallel with the high-level report, the researchers also released the detailed technical instructions for discovering vulnerable email gateways and for setting up a proof of concept email server, so organisations can assess themselves whether they are vulnerable to the direct email spool attack.
"Email was developed in the 1980s when security was not a concern. Back then, the internet was a quaint and friendly place" – Szathmari says. "Back then, email servers were open to everyone to send emails (called open relays). This practice was later abandoned due to the abuse by spammers. This relay feature is essentially why the direct email spool attack can work as it exploits a design weakness of the original SMTP protocol."
As the researchers explain in the report, to successfully protect a business from phishing attempts, organisations must ensure that the email gateways are set to accept email only from the IP addresses owned by the anti-phishing service of their choice. Without this essential last step, attackers can simply send malicious email directly to the organisation’s servers.
Phishing has become the leading threat to online security according to Telstra:
The two most common types of security incidents in Australia are Business Email Compromise (BEC) and phishing attacks. In Asia, the two most common are virus/malware outbreak and employee error; and in Europe they are phishing attacks and employee errors. These types of security threats highlight that cyber criminals are targeting employees who can be seen as the weakest link.
To exploit improperly configured email servers, attackers harvest information from a range of public sources to find the information they need to send email straight to an organisation’s servers.
"In our research, we relied on a combination of open data sources to identify the hostname of the relevant local email server running behind the anti-phishing solution at the organisations in-scope. Email administrators may think that by changing the MX records of the email service, bad actors will not be able to identify the connection details of the local email server. This is far from the truth, however, as various clues are available to reveal the hostname of the local email server."
Iron Bastion experts recommend that businesses to audit the configuration of their email services and/or seek for professional help to ensure that their anti-phishing solutions are correctly configured and safe from the direct email spool attack.
>>> Click here to read the detailed report <<<
About Iron Bastion
Iron Bastion are Australia’s phishing and cybersecurity experts. We provide cybersecurity consulting with specialised solutions to combat phishing. Our team are qualified cybersecurity professionals, and all our staff and operations are based in Australia.
Contact us for a free cybersecurity consultation or sign up to our managed services today.

